In the aftermath of the WannaCry attack that took the world by surprise, a new strain of the Petya ransomware made its appearance in late June in Europe.
The ransomware, dubbed Goldeneye by security experts, exploited vulnerabilities in the Windows XP operating system. The cyber-attacks were made possible by taking advantage of security weaknesses in users who had not installed the proper security updates issued by Microsoft.
Experts say the Goldeneye ransomware probably used EternalBlue, the cyber-weapon that was employed in the WannaCry attack after being stolen from the NSA. After kicking off in Spain and the United Kingdom, the malware has so far affected more than 200,000 users across 150 countries, including the US, Germany, Russia, and France.
Victims include the largest advertising agency in the world, UK-based WPP, oil giant Rosneft and steelmaker Evraz, both based in Russia, French industrial giant Saint-Gobain, Danish global shipping company A.P. Moller-Maersk, Deutsch Post, renowned law firm DLA Piper, and several ports around the world.

The attack also hit Ukraine particularly hard, devastating the country’s IT infrastructure. The cyber-attack affected the decommissioned nuclear power plant in Chernobyl, impacting its radiation monitoring system and forcing employees to do manual checks. The airport in Kiev as well as key government infrastructure, banks and energy providers in Ukraine have also been hit. Ukraine has quickly pointed the finger to Russia, suggesting that this was more of a deliberate cyber warfare act than a simple ransomware attack.
But no evidence has yet emerged supporting that claim, and security experts continued to treat it as a typical ransomware attack. Ransomware is a type of malware cyber-attack, during which the attacker locks the victim’s computer and encrypts their data, demanding a payment for unlocking and delivering the data back decrypted and safe. A ransomware attack exploits human, network, system, and software vulnerabilities to pierce through to the victim’s device, whether it is a computer, a smartphone, or other type of hardware like a printer or a point-of-sale (POS) terminal.
Usual methods to launch this type of attack include phishing e-mails or luring the victim into downloading and installing malicious applications, that in turn infect the affected user’s computer. Research suggests that it is usually human recklessness that allows ransomware attacks to take place, as almost half of them originate in spam or phishing e-mails and in 36% of cases, proper employee training could have averted the attack or mitigated the impact.
Infographic: Ransomware: Who’s Affected & Why | Statista
You will find more statistics at Statista.
In the case of Goldeneye, according to an article published on NewsBTC, the ransomware “posed” as a CV attachment in e-mails sent to HR departments of enterprises as part of a fake job application. According to the same source, the hackers demanded a payment of 1.3 Bitcoin – approximately $400.
Microsoft released an update aimed at fixing the flaw that enabled the WannaCry attacks, but not all users have updated their computers, thus allowing further attacks to be perpetrated. State infrastructure stakeholders, like hospitals and similar services, seem particularly vulnerable due to their out-of-date and largely neglected operating systems.
Source Article from http://www.hangthebankers.com/petya-ransomware-strikes-again-as-new-strain-dubbed-goldeneye-devastates-ukraine-and-europe/
 RSS Feed
RSS Feed















 August 5th, 2017
August 5th, 2017  Awake Goy
Awake Goy 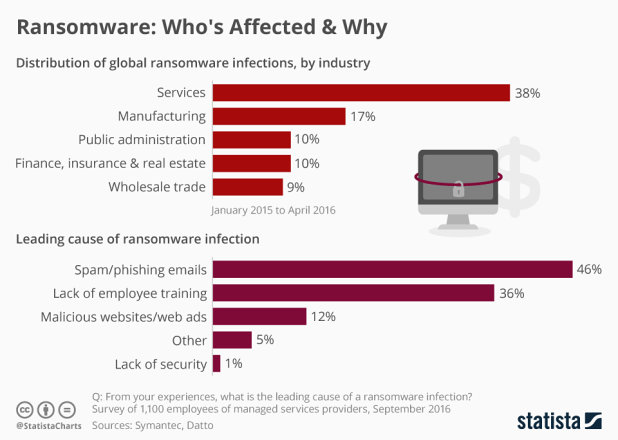
 Posted in
Posted in  Tags:
Tags: 













