How to Instantly Prove (Or Disprove) Russian Hacking of U.S. Election
By WashingtonsBlog
washingtonsblog.com
It’s newsworthy that CIA head Mike Pompeo recently met with Bill Binney – who designed the NSA’s electronic surveillance system – about potential proof that the DNC emails were leaked rather than hacked.
It’s also noteworthy that the usual suspects – Neocon warmongers such as Max Boot – have tried to discredit both Binney and Pompeo.
But there’s a huge part of the story that the entire mainstream media is missing …
Specifically, Binney says that the NSA has long had in its computers information which can prove exactly who hacked the DNC … or instead prove that the DNC emails were leaked by a Democratic insider.
Remember – by way of background – that the NSA basically spies on everyone in America … and stores the data long-term.
After the story of Pompeo’s meeting with Binney broke, Binney told Washington’s Blog:
Heres what they would have from the programs you list [i.e. NSA’s Fairview, Stormbrew and Blarney spying programs, which Edward Snowden revealed] plus hundreds if not thousands of trace route programs embedded in switches in the US and around the world.
First, from deep packet inspection, they would have the originator and ultimate recipient (IP) of the packets plus packet series 32 bit number identifier and all the housekeeping data showing the network segments/path and time to go though the network. And, of course, the number of packet bits. With this they would know to where and when the data passed.
From the data collection, they would have all the data as it existed in the server taken from. Thats why I originally said if the FBI wanted Hillarys email, all they have to do is ask NSA for them.
All this is done by the Narus collection equipment in real time at line rates (620 mbps [mega bits per second,] for the STA-6400 and 10 gbps [giga bits per second] for the Insight equipment).
Binney explained what these numbers mean: Each Narus Insight device can monitor and record around 1,250,000 emails each second … or more than 39 trillion emails per year.
Wired reported in 2006:
Whistle-blower Klein allegedly learned that AT&T was installing Narus boxes in secure, NSA-controlled rooms in switching centers around the country.
Binney told me there are probably 18 or so Narus recording systems throughout the U.S. deployed by the NSA at AT&T facilities, drawing my attention to the following NSA document leaked by Edward Snowden:
Binney has figured out their locations from publicly-available sources. He has also mapped out similar monitoring systems at Verizon facilities.
Binney also sent me hard-to-find company literature for Narus. Here are some interesting excerpts:
NarusInsight …
- Provides full visibility into network traffic …
- Analyzes at macro or micro level targeting specific or aggregate full-packet data for forensic analysis
And:
Universal data collection from links, routers, soft switches, IDS/IPS, databases, etc. provides total network view across the world’s largest IP networks.
Binney also pointed me towards a couple of network engineering principles that show that figuring out who hacked the emails (or proving they were leaked) is well within NSA’s capabilities.
Initially, when data is transmitted online, it is sent using the TCP/IP Packet format. Put simply, data is not sent in a vacuum, but rather as part of a bundle containing a lot of other information.
Here’s the TCP part of the bundle:

And here’s the IP part of the bundle:
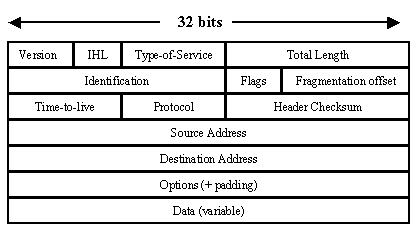
So any data analyst can learn a tremendous amount about the source address of the sender, the destination address of the receiver and a boatload of other information by using a “packet sniffer” to inspect the “packets” of information being sent over the web.
Additionally, it’s simple to conduct “traceroute” searches. “Traceroute” is a computer network diagnostic tool for displaying the route and measuring transit delays of packets across an Internet Protocol network.
Wired reported in 2006:
“Anything that comes through (an internet protocol network), we can record,” says Steve Bannerman, marketing vice president of Narus, a Mountain View, California, company. “We can reconstruct all of their’e-mails along with attachments, see what web pages they clicked on, we can reconstruct their (voice over internet protocol) calls.”
So NSA can easily basic packet sniffers and traceroutes, And see this.
And as Binney previously told Washington’s Blog:
As Edward Snowden said, once they have the IPs and/or other signatures of 28/29 [the supposed Russian hacking groups] and DNC/HRC/etc. [i.e. the DNC and Hillary Rodham Clinton], NSA would use Xkeyscore to help trace data passing across the network and show where it went. [Background.]
In addition, since Wikileaks is (and has been) a cast iron target for NSA/GCHQ/etc for a number of years there should be no excuse for them missing data going to any one associated with Wikileaks.
***
Too many words means they dont have clear evidence of how the data got to Wikileaks.
NSA either doesn’t have solid evidence of Russian hacking of DNC emails – which means the Russians didn’t do it – or those with the power to demand NSA produced the evidence simply haven’t asked.
View the original article at Washingtons Blog
Posted in Analysis & Review, Civil Rights and Privacy, Internet, Police State, Public Figures, War on terror.
– November 15, 2017
Source Article from http://feedproxy.google.com/~r/DarkPolitricks/~3/49MgxDER-Ag/
 RSS Feed
RSS Feed















 November 15th, 2017
November 15th, 2017  Awake Goy
Awake Goy 
 Posted in
Posted in  Tags:
Tags: 













