We are a non profit EU-COALITION AGAINST CYBERTORTURE and Task Force established to create awareness and more of Cybernetic Technology and electronic abuse, such as the illegal data collection and manipulation of humans via brain – machine – interfaces. Coined “Cybertorture” by the UN Special Rapporteur on Torture.

How do we protect people that by utilitarian grounds, without informed consent, are used for brain studies with brain-computer-interfaces in Cyber Psychological Systems, illegal stealing of brain data.
Currently there are no specific laws protecting humans, neither any medical support for them, during Cybertorture. The situation is created by the fact that scientists do not leave any information about the illegal mind reading technologies. They just keep on progressing in their cognitive neuroscience crimes.

This UN report include a definition of “Cybertorture” By the UN Special Rapporteur on Torture.
On February 28, 2020, the UN Special Rapporteur on Torture, Professor Nils Melzer, issued his World Report on “Torture and other cruel, inhuman or degrading treatment or punishment.” This report included a definition of “Cybertorture,” the Crime Against Humanity where millions of targeted victims worldwide are remotely assaulted with Electromagnetic Weapons in actions directed via computer, often from Supercomputers.
(A/HRC/43/49) Cybertorture:
1. A particular area of concern, which does not appear to have received sufficient attention, is the possible use of various forms of information and communication technology (“cybertechnology”) for the purposes of torture. Although the promotion, protection and enjoyment of human rights on the internet has been repeatedly addressed by the Human Rights Council (A/HRC/32/L.20; A/HRC/38/L.10/Rev.1), torture has been understood primarily as a tool used to obstruct the exercise of the right to freedom of expression on the internet, and not as a violation of human rights that could be committed through the use of cybertechnology.
2. This seems surprising given that some of the characteristics of cyber-space make it an environment highly conducive to abuse and exploitation, most notably a vast power asymmetry, virtually guaranteed anonymity, and almost complete impunity. States, corporate actors and organized criminals not only have the capacity to conduct cyberoperations inflicting severe suffering on countless individuals, but may well decide to do so for any of the purposes of torture. It is therefore necessary to briefly explore, in a preliminary manner, the conceivability and basic contours of what could be described as “cybertorture”.
3. In practice, cybertechnology already plays the role of an “enabler” in the perpetration of both physical and psychological forms of torture, most notably through the collection and transmission of surveillance information and instructions to interrogators, through the dissemination of audio or video recordings of torture or murder for the purposes of intimidation, or even live streaming of child sexual abuse “on demand” of voyeuristic clients (A/HRC/28/56, para.71), and increasingly also through the remote control or manipulation of stun belts (A/72/178, para.51), medical implants and, conceivably, nanotechnological or neurotechnological devices.1 Cybertechnology can also be used to inflict, or contribute to, severe mental suffering while avoiding the conduit of the physical body, most notably through intimidation, harassment, surveillance, public shaming and defamation, as well as appropriation, deletion or manipulation of information.
4. The delivery of serious threats through anonymous phone calls has long been a widespread method of remotely inflicting fear. With the advent of the internet, State security services in particular have been reported to use cybertechnology, both in their own territory and abroad, for the systematic surveillance of a wide range of individuals and/or for direct interference with their unhindered access to cyber technology.2 Electronic communication services, social media platforms and search engines provide an ideal environment both for the anonymous delivery of targeted threats, sexual harassment and extortion and for the mass dissemination of intimidating, defamatory, degrading, deceptive or discriminatory narratives.
5. Individuals or groups systematically targeted by cybersurveillance and cyberharassment are generally left without any effective means of defence, escape, or self-protection and, at least in this respect, often find themselves in a situation of “powerlessness” comparable to physical custody. Depending on the circumstances, the physical absence and anonymity of the perpetrator may even exacerbate the victim’s emotions of helplessness, loss of control, and vulnerability, not unlike the stress-augmenting effect of blindfolding or hooding during physical torture. Likewise, the generalized shame inflicted by public exposure, defamation and degradation can be just as traumatic as direct humiliation by perpetrators in a closed environment.3 As various studies on cyber-bullying have shown, already harassment in comparatively limited environments can expose targeted individuals to extremely elevated and prolonged levels of anxiety, stress, social isolation and depression, and significantly increases the risk of suicide.4 Arguably, therefore, much more systematic, government-sponsored threats and harassment delivered through cybertechnologies not only entail a situation of effective powerlessness, but may well inflict levels of anxiety, stress, shame and guilt amounting to “severe mental suffering” as required for a finding of torture.5
6. More generally, in order to ensure the adequate implementation of the prohibition of torture and related legal obligations in present and future circumstances, its interpretation should evolve in line with new challenges and capabilities arising in relation to emerging technologies not only in cyberspace, but also in areas such as artificial intelligence, robotics, nanotechnology and neurotechnology, or pharmaceutical and biomedical sciences, including so-called “human enhancement”.
1. Al Elmondi, “Next-generation nonsurgical neurotechnology”, Defense Advanced Research Projects Agency, available at https://www.darpa.mil/program/next-generation-nonsurgical-neurotechnology
2 See Human Rights Council resolutions 32/13 and 38/7. See, most notably, the 2013 disclosures by Edward Snowden of the global surveillance activities conducted by the United States National Security Agency and its international partners, see Ewan Macaskill and Gabriel Dance, “NSA files: decoded – what the revelations mean for you”, The Guardian, 1 November 2013.
3 Pau Pérez-Sales, “Internet and torture” (forthcoming).
4 Ann John and others, “Self-harm, suicidal behaviours, and cyberbullying in children and young people: systematic review”, Journal of Medical Internet Research, vol. 20, No. 4 (2018); Rosario Ortega and others, “The emotional impact of bullying and cyberbullying on victims: a European cross-national study”, Aggressive Behavior, vol. 38, No. 5 (September/October 2012).
5 Samantha Newbery and Ali Dehghantanha, “A torture-free cyber space: a human right”, 2017.

WHO WE ARE
 WHAT WE DO
WHAT WE DO
The European Coalition Task Force against Cybertorture is established to raising awareness to the legal systems as well as to the medical and scientific community to the crime of illegal biomedical and weaponry research committed on citizens in the European Union and beyond. As a European network, The Coalition acts as a lobbying and advocacy platform towards the EU and more. Using our international network of scientific and technology experts, partners in civil and human rights organizations as well as important stakeholders in civil society, we provide consultancy services to the EU Institutions based on our expertise. The Coalitions organizational goal is to influence EU legislation and the decision-making process in calling for a worldwide ban on weapons that might enable any form of manipulation of human beings.
HOW WE DO IT
- Awareness-raising campaigns to disseminate information and mobilize public opinion on the issue of covert CYBER technologies and techniques that enable the manipulation of human beings.
- Providing expert consultancy to key decision-makers on the creation of appropriate EU legislation to protect civil citizens from cyber covert crimes.
- Organizing networking events (workshops, seminars, conferences) involving all actors concerned to exchange experiences and best practices for the establishment of clear ethical boundaries to strictly regulate the use of cybersystems enabling the manipulation and control of human beings.

OUR PHILOSOPHY
It is our philosophy that all men are equal before the law. Everybody’s right to life shall be protected. Nobody shall be subjected to torture or held in slavery. Any technologies and techniques capable of endangering the human physical and/or psychological health, to modify the individuals’ autonomy and affect their dignity should be strictly prohibited.

Latest from the Blog
Researchers found a way to make AI learn intuitive physics like a human What’s happening Scientists taught a deep learning system to learn intuitive physics the same way human babies do. Why it matters This mechanism could be key in bridging the gap between humans and AI, as well as inform future psychology studies about…
non consensual experimentation is used for military purposes Changing Hearts and Brains: SOF Must Prepare Now for Neurowarfare By Dr. Shannon Houck, COL John Crisafulli, Lt Col Joshua Gramm, Maj Brian Branagan The timeworn “changing hearts and minds” idiom may soon take on a more literal meaning as we confront the weaponization of neurotechnology. In December…

Algorithmic power, NATO and Artificial Intelligence NATO has formally approved its first Artificial Intelligence (AI) strategy as it seeks a leading position in the adoption of AI for defence, but it may face some critical hurdles ahead in implementing the strategy, according to Simona Soare. NATO defence ministers have formally adopted the Alliance’s first artificial…
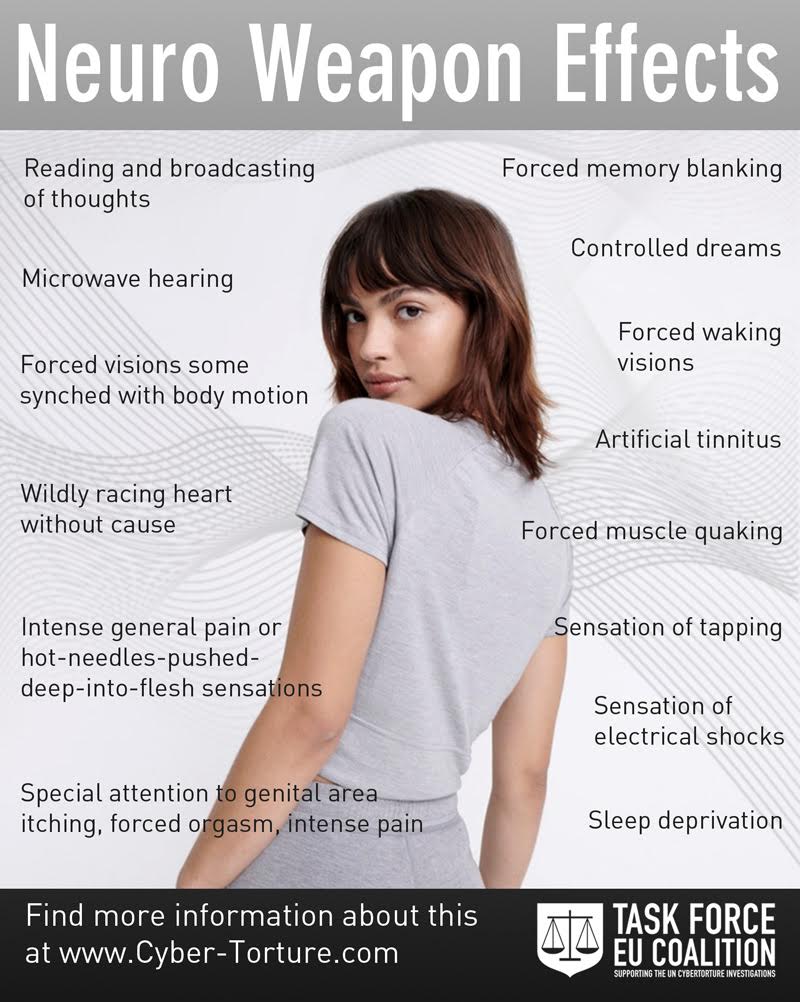
 Cyber Torture ” data-image-caption data-medium-file=”https://www.jewworldorder.org/wp-content/uploads/2023/04/appendix-189-cyber-torture-eu-coalition-against-cybertorture-homepage-cybertorture-organized-stalking-electronic-torture-the-targeted-individual-program-145.jpg” data-large-file=”https://www.jewworldorder.org/wp-content/uploads/2023/04/appendix-189-cyber-torture-eu-coalition-against-cybertorture-homepage-cybertorture-organized-stalking-electronic-torture-the-targeted-individual-program-114.jpg”>
Cyber Torture ” data-image-caption data-medium-file=”https://www.jewworldorder.org/wp-content/uploads/2023/04/appendix-189-cyber-torture-eu-coalition-against-cybertorture-homepage-cybertorture-organized-stalking-electronic-torture-the-targeted-individual-program-145.jpg” data-large-file=”https://www.jewworldorder.org/wp-content/uploads/2023/04/appendix-189-cyber-torture-eu-coalition-against-cybertorture-homepage-cybertorture-organized-stalking-electronic-torture-the-targeted-individual-program-114.jpg”>Related posts:
Views: 1
 RSS Feed
RSS Feed

















 April 21st, 2023
April 21st, 2023  Awake Goy
Awake Goy 
 Posted in
Posted in  Tags:
Tags: 
















